I managed to post three pieces on the blog in 2025 – hooray! It was a productive year despite the low post count.
I improved my ability to translate technical knowledge to the appropriate audience. At the same time, I maintained a steady cadence of developing and maturing my digital forensic and investigative skills. I believe this progress allowed me to be a more effective ambassador and board member for HTCIA’s Northern California chapter, and an influential program lead aligning digital forensic and investigative techniques to incident response for my employer. The knowledge and takeaways from reading books like Implementing Digital Forensic Readiness: From Reactive to Proactive Process by Jason Sachowski, and Placing the Suspect Behind the Keyboard: DFIR Investigative Mindset by Brett Shavers have been instrumental.

While not included among the subjects I synopsize below, I also collaborated in research that was posted on a blog early in 2025 (The Challenge of Tracking SSH Connections Without System Logs), and I was a guest on a new podcast, Securanoia, in December.
Completely unrelated to anything I’ve done before; following an unexpected personal project that spanning December 2024 and nearly the entire first quarter of 2025, I am more knowledgeable about teapots and ceramics than I care to be. Finding appropriate/meaningful homes for a collection that was meticulously curated over decades was no small feat. With the exception of one piece, they all found good homes.






I was able to walk an average of 1,000 more steps a day compared to last year. That’s awesome. I feel awesome. I will walk more.
I was fortunate to be able to get away from work as much as I wanted to spend time with family. Since my son started transitional kindergarten (TK) at a school based on Waldorf education, I’m doing other cool things for his class.
Though I’ve hardly written, my social “digital forensic and incident response” cup is full because of those I engaged with on social media or in person. Thank you.
On Art
LEAPPs
Knee-deep in ceramicware, I sought refuge in an opportunity to artistically contribute to the LEAPPs development team. The goal was to create a graphic for each of the LEAPPs and soon-to-be released LAVA. After a handful of iterations, we came up with…


It’s awesome to see these adopted as enthusiastically as they have been. I also get a kick out of seeing them appear in public presentations, like at SANS.
MrEerie “mystery” Ghost
I’ve been exploring my vision of what I’d like a “mreerie/mystery” ghost to look like, and I asked for help from David Hansen (aka thromgard). I believe these look awesome – way cooler than my original goofy ghost.
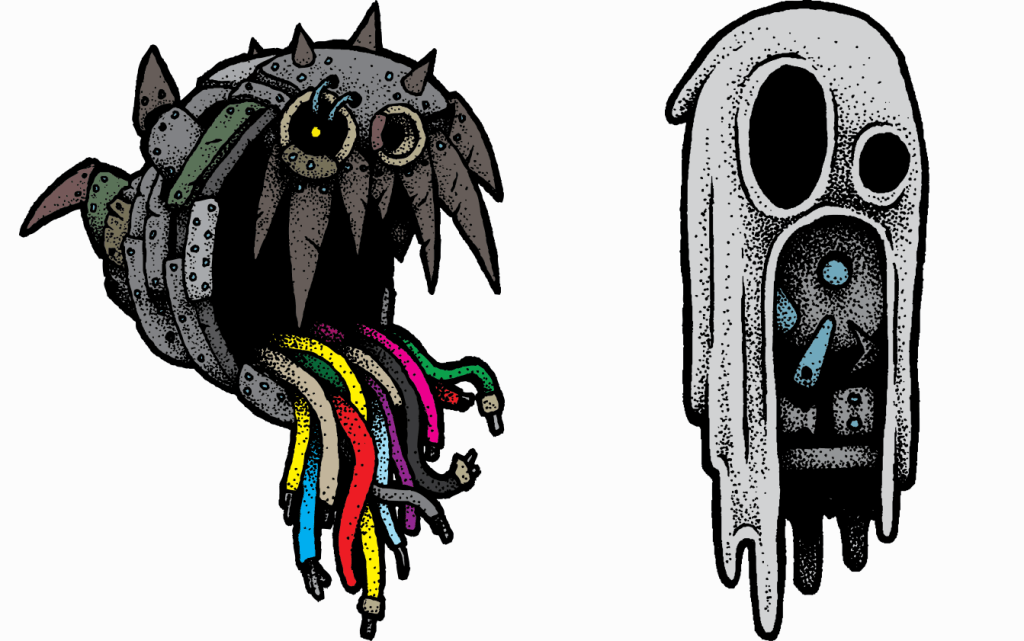


Arts/Crafts at TK
Since my son started TK, I’ve been lending what artsy and crafty capabilities I have. Fixing classroom toys has also been an exercise in creativity!





Taking time to explore my creative side is a joy, and it’s especially fulfilling when others appreciate it as well.
On Blog Posts
Switching gears from ceramicware to digital forensics and incident response for the blog in May, X-Ways’ introduction of BitLocker support in X-Ways Forensics was a cool update that got me back into a brief groove. Shortly after, I released a post on exploring Andrea Lazzarotto’s open-source tool, Fuji, to better understand the native macOS commands behind the tool. Prior to enrolling in FOR608, I wrote a quick update on a requested feature added to DeepSpar’s Guardonix and USB Stabilizers.
On HTCIA
Continuing to serve as a board member for the 2024-2025 cycle, the Northern California chapter resumed HTCIA’s mission of providing learning opportunities to its members and guests.
We started our first meeting of the year in February with a presentation on WinFE by yours truly. Brett Shavers attended! In July, board members, Aaron Reyes and Greg Tassone, presented on practical application of Hashcat in corporate and law enforcement investigations. Coincidentally, Hashcat v7.0 was released shortly after. In October, Steven Nguyen presented on physical security with a focus on mechanical locks. Steven really brought the shop in-house for this presentation. For our last meeting of 2025, Cynthia Navarro gave a presentation on OSINT. For the hands-on lab, we learned more about Cynthia using the OSINT techniques she presented on.

Preparing for my first public speaking event presenting on WinFE, I was supported by Brett Shavers and Mark Spencer. I was given access to get hands-on experience with Arsenal Image Mounter‘s Remote Agent and I shared parts of my exploration online before giving the presentation.
- Initial exploration of the AIM Remote Agent
- Imaging an Intel Ubuntu disk over the network with AIM Remote Agent
- Virtualizing an Intel Windows disk over the network with AIM Remote Agent
- Booting WinFE on a “target machine” from a PXE server, then mounting the target machine’s disk to the forensic workstation over a network
Many local professional groups provide great value, but I believe HTCIA is unique in its focus on investigative skills that promote fairness and objectivity. I feel fortunate to play a role in supporting and co-facilitating these learning opportunities.
On Upskilling
Renewing the X-Ways X-PERT Designation
Despite its vendor and tool focus, renewing my X-PERT designation from X-Ways Software Technology AG was a meaningful accomplishment – for a couple of reasons. First, I didn’t perceive the renewal attempt to be any easier. Second, I invested time and resources to become proficient with the tool over three years ago; it was satisfying to demonstrate to myself that I’ve maintained enough proficiency to pass again. For context, you can read about my growth with X-Ways Forensics.

Sumuri’s MFSC Series and the CFME
After completing MFSC-101 last year, I used tuition reimbursement again to complete MFSC-201 in February. After catching up, but just before jumping into FOR608, I achieved the CFME designation. I fully intend to summarize my experience and takeaways completing Sumuri’s MFSC series, especially compared to FOR518, sometime in 2026.

SANS FOR608 and the GEIR
One of the most surprising things I found value in FOR608 is the operational side of incident response, including concepts like incident resource management and adapting frameworks like Crew Resource Management. FOR608 course author, Mathias Fuchs, recently wrote a related piece discussing the unique psychological challenges (cyber) security personnel experience.
I enrolled in FOR608 for a couple of reasons:
1) FOR608’s curriculum covers practical applications and provides an overview of multiple platforms you’re likely to encounter during enterprise incident response. This aligned well with what I wanted to accomplish at work for the year and was a good fit for my goals.
2) FOR577 didn’t have a certification at the time when I submitted the request to my employer (almost a year prior). While certification wasn’t a requirement of my employer, it was a personal preference. When it was time to sign up for FOR608, FOR577’s certification, GLIR, was available, I didn’t bother requesting a change.
I’ve completed a handful of SANS courses (FOR500, FOR508, FOR509, FOR518, and FOR585), so most of the artifacts reviewed in FOR608 were familiar, with the exception of the Linux module, from which I learned a lot. Even with the partial review, the class provided significant value, particularly in reinforcing and validating my approach to large-scale collection and analysis at work.
Techno Security East
I did not plan on attending any conferences this year. When I received a complimentary ticket to Techno Security East, I made arrangements to leverage the opportunity and make it happen.
While there was no shortage of great topics, a couple stood out to me.
Matt Danner, of Monolith Forensics, presented a case study concerning an alleged insider threat. It was a great discussion of digital forensic techniques applied to the case and the use of an investigative mindset to combat assumptions throughout the process based on the information available.
As someone interested in learning how digital forensic examiners prepare and testify in court; Bill Aycock’s presentation on mastering the art of expert witness testimony offered great insight.
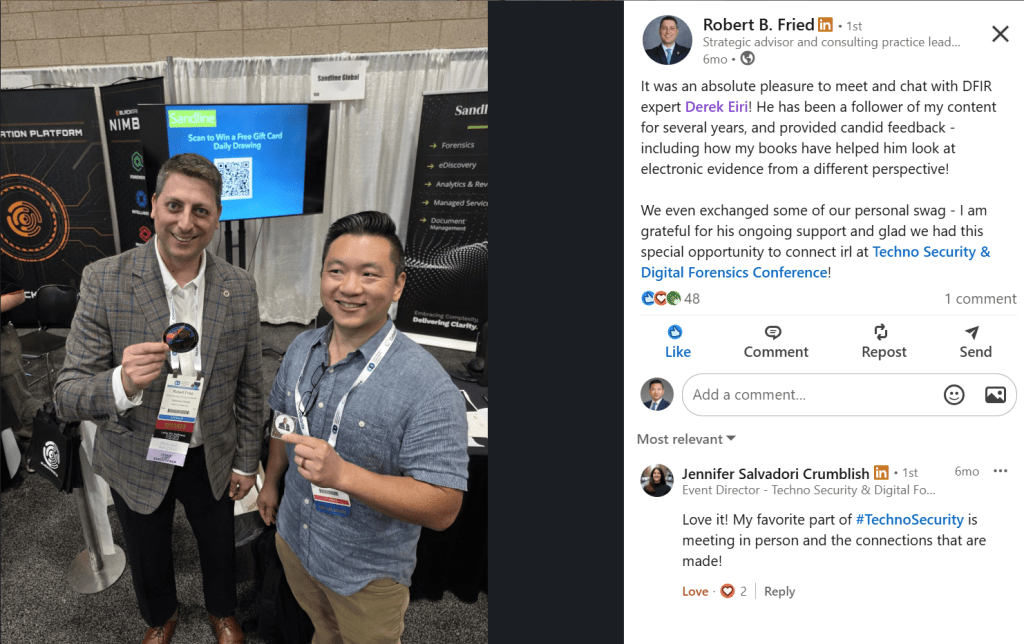
It was also great to finally meet and converse with several investigators who are at the top of their respective fields and disciplines. I’ve been following many of them on social media for some time. Among them were Robert Fried and Jerry Bui.
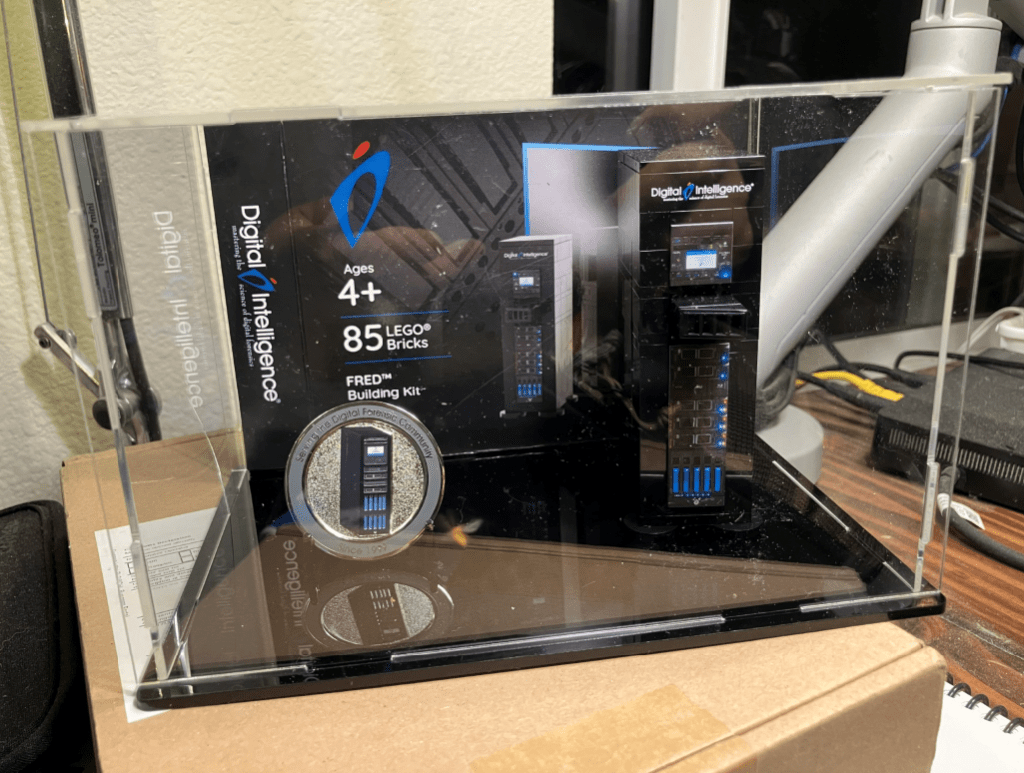
Techno Security East executed a cool exhibit hall scavenger hunt. By participating and completing it, I won an annual subscription to OSForensics. The Digital Intelligence FRED LEGO set was also a really cool promotional swag item.



My son really appreciated me taking home “Duck”, also from Digital Intelligence.
On 2026
I will continue my role as a board member for HTCIA’s Northern California chapter for 2026. Following a change, the chapter board member term is now one year.
2025 was an especially productive year in my paid role. I plan to build on this momentum by implementing initiatives that leverage automation and significantly improve scalability. If I have an opportunity to explore employer sponsored structured learning like FOR577 or from Memory Analysis, I’ll tackle that enthusiastically.
I still have chickens, though a few seemed to have wandered off; I’ll occasionally spot these wanderers visiting.
I’m looking forward to what I will experience with my son next.
I’ve hesitated for the longest time because of their size and maintenance, but I’m considering a treadmill.
Here (on the blog) and everywhere, thank you for your time and attention in 2025. Lets do it again next year.
Feature image generated with WordPress’ Jetpack AI Assistant.






Leave a comment